Karen
Sam
JP
- PGP Keys
- Vossen's Law
- Firefox
- MythTV
Photos
- Deck
- SCUBA
- Dolphins
Security
- Firewall Rules
- Flypaper
- GNATBox
- Home
- Home Net Security
- Principles
- Snort
- Snort Books
- Sec Tools
- GenPass
- Honeypot Stats
- Firewall Stats
Source
- Perl
Networking
- Time
- NAT
- IP Calcs
Linux
- apt
- Edutainment
- SME Server
- Backup (DI-30)
Windows
- Win Tools
- Voodoo
- Win. Shell Scripting
- POSIX Redirection
- Winlogcheck
What's New
Email me
Email Form
The Risks...
Are real.
There is no security through obscurity. While is it true that it's very unlikely that someone will specifically try to hack you, that doesn't matter! There are a large number of hacking tools that simply scan a range of IP Addresses (similar to telephone numbers) for a vulnerability. If you happen to have an IP Address in the target range, and if you happen to have that vulnerability--you are hacked--simple as that. :-(
Here are some statistics from the firewall at my house. I do not have a web server, or anything "tempting," these are just the random scans or "doorknob twists" I just described above. When I wrote this in mid 2002, on an average week, 88 different people tried to attack 41 different services 252 times. At my house!. It's worse now. See my current cable modem firewall stats.
So who cares if they break into my machine? Well, here are some things to think about:
- Do you use Quicken? One Russian hacking ring targeted Windows machines expressly to steal Quicken files. Are your Quicken files password protected? It doesn't matter--it's trivial to crack that "protection."
- Do you have information from work on a home PC, or is your work laptop connected? It would be a lot easier to hack your house than to hack you at work.
- You could become a "zombie," that is, one of hundreds or thousands of computers used to launch distributed denial of services attacks such as the one that brought down Yahoo and Amazon last year.
- You could become a bounce point used to conceal an attacker hacking someone else. Wouldn't it be interesting to have the Secret Service show up one day because your PC was attacking Whitehouse.gov?
Adding a wireless connection only increases your security risks. See below for more information. Wireless can be done securely--or securely enough anyway--but that entails more work. Security is not "plug and play."
Having said all that, dial-up connections are somewhat less of a risk, as are some types of cable modem. The difference is that with a dial-up connection or a cable modem that uses PPPoE (Point-to-Point-Protocol over Ethernet) and/or DHCP (Dynamic Host Configuration Protocol) your IP Address is different each time you connect to the Internet. Thus, even if you got hacked, the hacker may have more trouble finding you again. Note that same cable modems that use DHCP still get the same address each time, so this is not a help. Also, depending on how you were hacked and for what purpose, different IP Addresses may not matter. For example, some kind of program may b installed to actively tell the hacker what your new address is every time you connect.
The bottom line is that no matter how you connect to the Internet there is a risk, and you should do everything you can to minimize that risk. If you are just a bit more difficult to get into than the next guy, the hackers will go after him instead of you. And if the various scanning tools can't find the vulnerability, they will pass you by. The Internet is far too valuable not to connect to--just understand the risks and try to mitigate them.
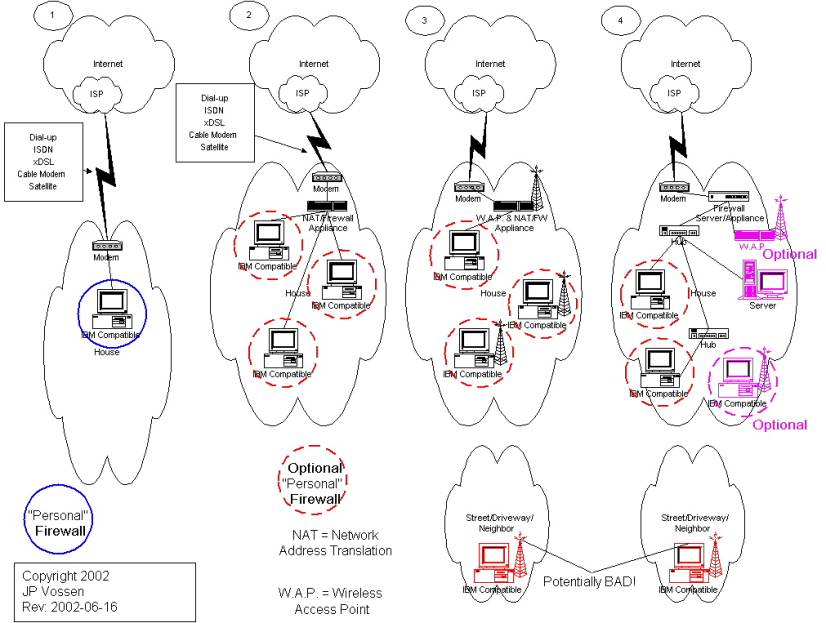
Typical Home Network Designs
See the diagram below.
Note: this architecture is not suitable for hosting services, such as a web site or e-mail server, on your home LAN. For that you need to implement a DMZ, which is out of the scope of this document. Hosting services may also be against the terms of service of your contract with your ISP.
Links
| Link | Speed | Cost (estimates) | Availability |
|---|---|---|---|
| Dial-up | Slow | $15-25/mo | Almost always |
| ISDN | Medium | Expensive, and charged per minutes | Usually |
| xDSL | Varies | Depends on type of DSL and distance from phone company Central Office (CO)-($40-350/mo) | Depends on distance and if the service is available in the area |
| Cable Modem | Varies-Fast | $35-60 | Depends on cable company |
| Satellite | ??? | ??? | ??? |
1. Simple/Home
This is the most common situation. Whatever link is used is just connected to 1 PC and that's it. Unless a "personal" firewall is used, there is very little security, especially on Windows 95/98/ME. Windows NT, 2000 or XP can be made somewhat more secure, but the default installation is not secure. In other words, unless you have taken additional (and sometimes complicated) steps to secure it, it's not secure at all.
2. NAT/Firewall Appliance
There are three types of NAT or Firewall appliances in the SOHO market. These are listed below in order from least to most secure. The price tends to follow that from cheapest to most expensive, but there are exceptions.
NAT Device
This is a step better than option 1 and it allows you to connect more than 1 PC to the link. However, NAT (Network Address Translation) does not provide that much protection. NAT provides translation between the public, routable IP Address you get from your ISP when you connect to the Internet and a private, non-routable address that you can use on your internal network. Any PC can make a connection out, and the reply to that request is allowed back in. This is not nearly as secure as it sounds, but it's better than nothing.
Firewall
Using a firewall builds on the NAT device. It will virtually always use NAT as well, but it adds rules that allow you to define what types of traffic are allowed in and out. A simple packet filter firewall is better than NAT, but it also has some security problems. To vastly oversimplify the problem, packet filters only look at what the packet of data says it is. It's very easy to make a packet lie, and a packet filter will usually not catch it.
Stateful Firewall
A stateful firewall builds on the packet filter and keeps a "state table" of what connections are in progress. This way, if a packet tries to lie and say that it is part of an established (and thus presumably allowed) connection, but that connection is not listed in the table of allowed connections, it is denied. This is about as secure as you are going to get in the SOHO environment.
The next level of security involves using application level proxies, which you will not find in typical SOHO devices and which are outside the scope of this paper.
3. Wireless Appliance
Using a wireless appliance is very similar to option 2, except it adds wireless capability. The same three levels of security from above may usually be found in wireless devices as well. But wireless adds complexity and vulnerability due to the fact that it is wireless. Now I can site in the street and use your Internet connection to surf, or to hack someone. If I live next door to you, and my parents have restricted my Internet connection, I may be able to use yours to get around those restrictions.
4. Complex/SOHO
This is a complex network, connecting multiple PCs in different areas, and optionally supporting servers, segmented wireless access and more. Anything this complex is getting out of the scope of this paper.
Terms
| DHCP | Dynamic Host Configuration Protocol, a protocol used to automatically assign IP Addresses to devices when they ask for one. |
|---|---|
| Firewall | Software or hardware intended to provide a separation between trusted and un-trusted networks. Firewalls often allow you to create rules to define what kinds of traffic are allowed to pass between the different networks. |
| ISP | Internet Service Provider. The service that connects you to the Internet, e.g. AOL, MSN, etc. |
| NAT | Network Address Translation, also called masquerading. The process of segregating any number of illegal, non-routable or private IP addresses behind a single or small number of legal, routable or public IP Addresses. |
| Personal Firewall | A program you install on an individual PC that acts as a firewall. These are often relatively simple and may not allow arbitrary rules to be created. |
| PPPoE | Point-to-Point-Protocol over Ethernet, a method some cable modems use that establish what looks like a dial-up connection over the cable modem. In other words, you "log in" with a user name and password to get the cable modem to work. |
| SOHO | Small Office/Home Office, the environment for which this paper is intended. |
| Stateful Firewall | A firewall that keeps track of existing and allowed connections in a "state table." More secure than a non-stateful packet filter type firewall. |
Resources
See the diagram below and my SOHO Security section.
History
| Revision Date | Comment |
|---|---|
| 2003-11-09 | Converted to HTML and minor revisions |
| 2002-05-26 (and thereabouts) | First public release |
| 2002-06-16 | Corrected diagram (I left the "modem" off of #2-4) |
4 Typical Home Network Diagrams